Cryptographer: Lots of people have been asking “how do I encrypt my email” or “how can I hide from NSA surveillance”. It turns out that the answer to the first question is fairly straight forward, while the second is not, so lets look at encryption first.
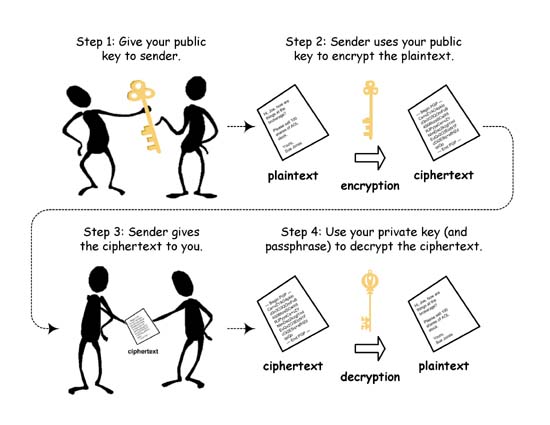
The Physicist wrote about the details of cryptography here. The real magic is in the public key systems like RSA or Elliptic Curve cryptography. Before the invention of public key cryptography, you had to securely exchange secret keys with everyone with whom you might want to communicate. So any time you wanted to communicate with someone new, you had to create a new key, and then somehow get it to the other person in a way that you could be sure would not be intercepted. With public keys, you just need to create one key, or actually a key pair. One of them is called the public key, and the other the private key. The amazing thing about these is that if the public key is used to encrypt something, that same key can not be used to decrypt it. The math on that is kind of amazing, so you might want to go back and read that earlier article.
This is wonderful, because we don’t need to worry about protecting the public key. You could paint it on your house, or publish it in the newspaper. Literally anyone can get it and use it to encrypt a message to you that only you will be able to read. The only trick is, how do they know that the public key is actually yours. What if some evil cryptographer decided to graffiti his key on your wall? Then everyone would be encrypting messages intended for you with his key so he would be able to read them.
In most public key systems, it also works the other way, so if the private key is used to encrypt the message, then only the public key can decrypt it. This might seem like a daft thing to do, to encrypt a message that absolutely anyone can read, because they all have access to your public key.
But wait….. only you could have created that encryption that they all can decrypt, so it acts like a signature. It assures the reader that the sender had access to your private key (and hopefully you have taken care that no one but you does).
This also helps take care of the “is this really your key” problem. If there are some people that we all trust, they can sign a certificate saying that “this key here belongs to this person with this email address” or to a specific website, or whatever. These entities are called Certificate Authorities.
You already use all this all the time when you visit secure websites. If you see the lock icon in your browser, or the URL starts with “https://”. Behind the scenes, the website is using public keys to handle the encryption of the page, and you know you are talking to the real website because the key and the domain name are in a certificate signed by a certificate authority. There are vulnerabilities in all this, but that is a subject for another post.
Email encryption is much less common. Now obviously I am not suggesting that you bust out a calculator and do some really large number exponentiation in a galois field every time you want to send your friend an email. Fortunately, all the heavy lifting has been taken care of for you. There are two widely used standards for email encryption: SMIME and PGP.
SMIME is a standard built into most email clients, including on iOS and Android. All you need to do is get an SMIME key and certificate. Several companies provide free SMIME certificates, of which the best known is Comodo. They only verify that the key you generate corresponds to your email address, by sending a confirmation email. Higher levels of authentication are available at a price.
Once you follow the instructions and install the certificate in your mail client, it will automatically sign all of your outgoing email and include a copy of your public key and certificate. If you receive a certificate from someone else, it will be stored on your computer, and used to encrypt any future emails to that person automatically.
PGP, and its free open source doppelganger GPG, work slightly differently. You will need to download and install the GPG software and plugins for your email clients. PGP / GPG support for mobile devices is a mixed bag at best. There are several advantages to using PGP / GPG however. First, you have complete control over the key generation process, and can create much longer keys than are available from SMIME providers. Second, you don’t need to trust some central certificate authority. Instead PGP / GPG use something called a web of trust. You personally sign the keys that you receive directly and securely from people you know. This make you like a micro certificate authority. You can then decide how much you trust people you know to verify keys from the people they know. This builds up a trust network whereby you can confirm the authenticity of keys without any one central trusted provider.
One problem with both of these email encryption solutions is that they leave a lot of information out in the clear. The To: and From: addresses need to be exposed, or the email won’t get delivered, and replies would not work. The Subject: line is also left unencrypted because …. reasons. So, anyone watching your communications can see the subjects you are talking about, and who you are talking with, and probably who they are talking with. This quickly builds up a very detailed and accurate picture of your personal social networks. For example, if you are a dissident, even if the government can’t read your messages, they know you are a dissident because a large fraction of your communications are with other known dissidents.
The same applies to secure web pages. The attacker may not know the contents of the pages your are visiting, but he does know the website you are visiting. If that page is http://deathtotyrants.org you are not leaving them a very hard puzzle to solve.
This kind of threat is called “traffic analysis”. Hiding your traffic patterns turns out to be much more difficult than hiding the contents of your messages.
There are a number of anonymity services which will help with this. TOR is free, and there are many paid options. All of these require a degree of trust in the operators, which is a trick with TOR since you don’t actually know who they are). If you use them to simply access public information, then it is difficult to do traffic analysis, but if you have any accounts out there, then you start giving away a lot of information. If you set up a gmail account through the service, then Google does not know who you are (if you make sure to get rid of all old Google cookies, or use a clean computer just for this). However, all the people you email from that account would be connected to that account and to each other by traffic analysis. Furthermore, if you communicate with the same set of people anonymously as you do under your real name, then that can be used as a very unique fingerprint to connect your anonymous account to your real identity. The same applies to any other kind of social media site.
You could use a different social media or email account for every single person you communicate with, and make sure that you change anonymous addresses and clean up the computer between each one. You would also have to make sure that you never ever make any mistakes, because log files live forever, are easy for governments to obtain, and can undo all your other work.
So, best of luck, and let me know how that tin foil hat is working out for you.





Wait a minute…. isn’t the whole point of networks like TOR and I2P to make surveillance difficult, even if many operators are compromised?
Please note that the “free SMIME certificates” provided by Comodo are not secure in that Comodo generates and knows not only the certificate, but also both the public and private keys violating the requirement that only you know the private key.
And of course all (normal) forms of encryption are eventually vulnerable to sheer brute forcing. The amount of time and energy required varies depending on the technologies involved but a sufficiently resourceful entity (like say a government) with time and effort could theoretically break through almost anything.
Whether or not any of that is practical or not depends both on the technologies in play and if anyone is willing to put that much work into it, but if someone is really, really determined to break your encryption they probably will eventually.
Have a read about ‘speed hashing’. It’s both fascinating and scary in equal measure!
http://www.codinghorror.com/blog/2012/04/speed-hashing.html