Physicist: Freaking terrible.
The Enigma machine used a “rolling substitution cypher” which means that it was essentially a (much more) complicated version of “A=1, B=2, C=3, …”. The problem with substitution cyphers is that if parts of several messages are the same then you can compare their similarities to break the code. Enigma was broken in part because of German formality (most messages started with the same formal greeting). Even worse, since some letters are more common than others (e.g., “e” and “g”) you can make progress by just counting up how often letters show up in the code (or even get an idea of what language the code is written in without breaking it!). Substitution cypher are so easy to break that some folk do it for fun. Rolling substitution cyphers can use a set of several encoding schemes and cycle through which code is used or make the scheme dependent on the previous letter, but this merely makes the code breaking more difficult. Ultimately, all substitution cyphers suffer from the same difficulty: similar messages produce similar looking codes.
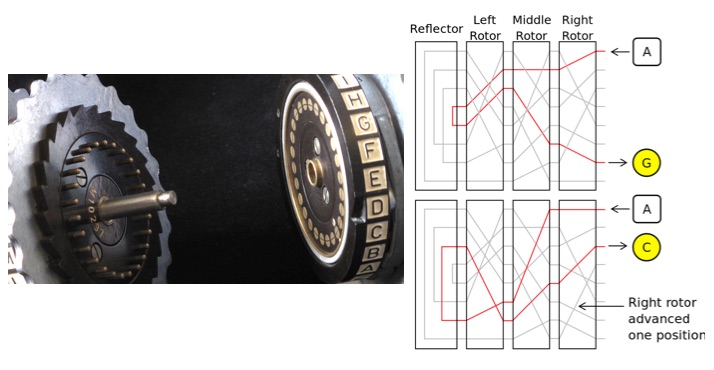
Enigma used three rotors which rotated after each letter was pressed allowing them to generate a huge number of different substitution cyphers, using a different one for each letter. Still: what your cellphone uses is much, much better.
Modern cryptography doesn’t have that problem. If any part of a message is different at all, then the entire resulting code is completely different from beginning to end. That is; if you encrypted a message, you’d get cypertext (the encoded message) and if you were to encrypt the exact same message but misspelled a single word, then the cypertext would be completely different.
If your messages were “Hello A”, “Hello B”, and “Hello C”, then a substitution cypher might produce “Tjvvw L”, “Tjvvw C”, and “Tjvvw S” while RSA (the most common modern encryption) might produce “idkrn7shd”, “62hmcpgue”, and “nchhd8pdq”. In the first case you can tell that the messages are nearly the same, but in the second you got nothing.
Enigma was very clever but is shockingly primitive compared to modern crypto techniques. If anyone in WW2 had been using modern (1970’s or later) encryption, then there is no way that anyone would have been able to break those codes (and Turing would have to settle for being famous for everything else he did).
There’s a post here that talks about the main ideas behind RSA encryption. The really fancy stuff is some of the only math that isn’t publicly known. Scientists have a whole thing about openness and the free exchange of information that governments and corporate entities (for whatever reason) don’t.

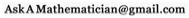




While this is certainly true overall about the strength of RSA vs. most substitution ciphers, for the sake of pedantry I feel like I ought to point out that the only possible perfect encryption scheme is essentially a variation on the Vignere substitution cipher. 😛
Why germans did not randomize fixed length initial part of the message ? e.g, with 30 random letters (keystrokes) that would set set the random initializaiton vector for the message.
This comparision is really like comparing apples with peaches.
RSA is an asymmetric cipher, which Enigma is a symmetric cipher. So it would be better to compare Enigma to something like AES. Doing a naive comparison there would be (based on Kerkhoffs Law) that Enigma has a key space of about 14 bit. Which IS really terrible compared to todays standards. But nothing a person could do with pen and paper.
BTW, also the examples with “Hello” do NOT apply to Engima, as the double “L” would be enciphered most likely with a different letter (you got it correct, when you called Enigma a “rolling” substitution cipher).
Firstly, many thanks for this website, it makes life more interesting.
Now, about the ENGIMA and what has been stated about it above. Part of what I say has already pointed out by Mr Idran.
There were weaknesses in the Engima, no doubt, and (as important, more or less), in the way that it was used, that led to its successful cryptanalysis. eg a letter can never be enciphered as itself, the stepping is predictable, a rotor used in one place can never be used in the same place the next day, ‘cillies’, rigidly structured messages etc.
However (and this is my grouse), one feels that the article implies that the cryptanalysis of the ENIGMA was a trivial task, which it most definitely was not. In addition, the article seems to imply that the cryptanalysis of the ENIGMA was comparable to that of the substitution ciphers, which, if intended, is extremely misleading.
Also, the substitutions of the Enigma, in a given setting, would repeat only after 17,576 characters (or 456,976 in case of a four rotor ENIGMA), whereas the message lengths were, as per regulations, much shorter than that. In case there was a longer message it would be split up. For details of repetition (17,576 etc) see the wikipedia page for the ‘cryptanalysis of the ENIGMA’, for message length, see this link (many more can be found on the net) :
http://www.enigma.hoerenberg.com/index.php?cat=M4%20Project%202006&page=Publication
So, counting the frequency of letters would not be of much help.
The setting itself was (partially) randomly arrived at by the operator, and (otherwise) determined by the signal instructions for the day, which were distributed on paper. The part of the setting randomly arrived at by the operator made it difficult to directly compare two messages, unlike what could be done with a simple substitution cipher.
“ If anyone in WW2 had been using modern (1970’s or later) encryption, then there is no way that anyone would have been able to break those codes “ seems to imply that all forms of encryption used in World War 2 were breakable. If that is what is meant, then it is wrong. The One Time Pad system (see link given by Mr Idran above) was very much in use during and before World War II, and cannot be broken, even today, and in the foreseeable future. It is logically impossible. Some one may steal the code books and then decipher it, however that is not cryptanalysis. As a matter of interest, one may refer Wikipedia for ‘Venona project’.
Similarly, ” Rolling substitution ciphers can use a set of several encoding schemes and cycle through which code is used or make the scheme dependent on the previous letter, but this merely makes the code breaking more difficult. ” True, but a substitution cipher which does not involve cycling through, and which is used only once, and whose patterns are not regular, becomes unbreakable. A simple substitution, but unbreakable. Details are in the Wikipedia link given by Mr Idran. It can also be described as a “Vignere cipher with a random key that is (a) at least as long as the message and (b) used only once”.
Perhaps the word ‘Rolling’ (as used in the article) should be defined.
On re-reading, this comment/response seems somewhat curmudgeonly, which is not the intention. I thank you once again for this website, I keep lurking around here quite a lot.
Also, there are many ENIGMA enthusiasts on the web, it is surprising that there are only four comments so far.
Here’s some videos on the Enigma code that explain how it works and the history behind it very well.
http://youtu.be/G2_Q9FoD-oQ
http://youtu.be/V4V2bpZlqx8
Does anyone know how they handled numbers using enigma? I assume that their encrypted communications would need to include things like dates, time, number of tanks, coordinates, etc. but all of the Enigma websites and pictures I’ve seen only the encryption of letters. Would they spell all numbers out as in “twenty two tanks” or “attack at six twenty am on Tuesday December fifth” ?
Larry, thats how they did with numbers. I’ve seen a couple of deciphered original messages on german web pages.
What I’m wondering is, for fact we know that with todays tools a enigma message can be deciphered quite easily.
Why is there a BOINC group (enigma project) still working on deciphering, yet not deciphered original messages from WWII?
I dunno. The RSA CAN be Cracked with quantum computers, and there may be a formula to crack long prime nos. in the future. If the German Operators had not been Idiots, it would have been Tough to Crack. But, also, why not use an ideagram alphabet like Chinese
1. WAyyy more possibilities
2. frequency analysis would Not work with words, as opposed to letters
@Idran…for the sake of pedantic pedantry, I submit, the only perfect cypher is to say nothing at all 🙂
Years ago, the Australian Corp of Signals used a on time tape machine called
the BID30, unless you could get a copy of each tape before it was burnt, you COULD NOT break the cypher. In fact, as the machine worked in a synchronous mode, meaning the one time tape was always being sent, you DID NOT know if a message was even being sent. Unbreakable with a big capital E.
Hello,
There is a better cipher machine known as the Galaxy Cipher Machine on various sites on the web. It is easy to make, use, and impossible to break.
Regards, Russell Lee